After a good tip on Hackaday I picked up an X-rite RM200. A tool with no real use to virtually anybody, yet has provided a huge amount of entertainment to me and at least a handful of others (and not by going around testing the colour of everyday objects).
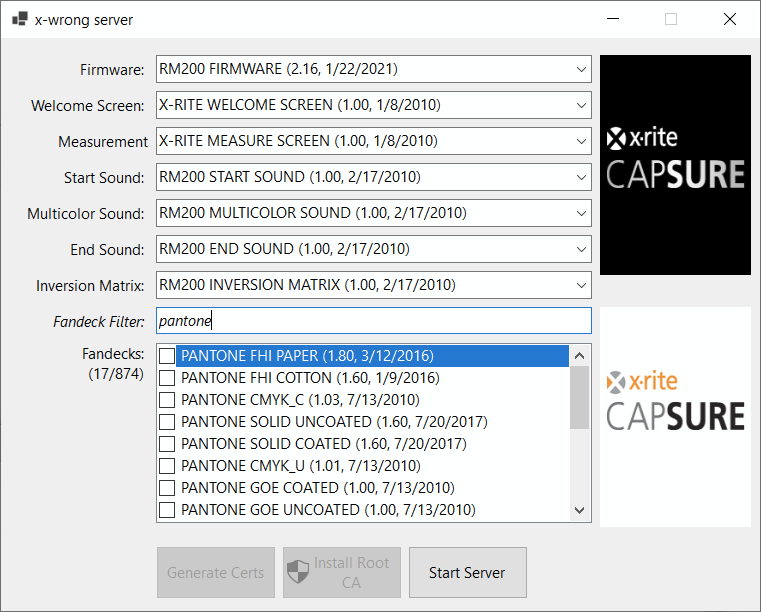
The original hack for these was to intercept the update request (using Fiddler) and swap the serial number, to get hold of different firmware and colour fandecks. This allowed a cheap cosmetic model (which can be found on eBay, often very cheaply) to be turned into the more expensive regular model. Using the information provided, that took all of 2 minutes to do to my own one. After a further 2 minutes of playing with the upgraded device, I wanted to do something more fun with it. So, first job, set about improving the hack process. Instead of intercepting the request to monkey with, why not write my own server for the sync application to connect to, then I can feed it whatever files I want.
That turned out to be quite easy, so on to the next challenge… That’s when I stumbled on Ivor Hewitt’s blog, another keen hacker who had picked up an RM200 for the same reasons.
Lots of emails were exchanged and a lot was figured out. As Ivor had already opened his to connect up a j-link, and I wasn’t keen to do this to mine unnecessarily, this meant Ivor was taking most of the risk on the dicier commands. When bootloader SPI flashing was just about figured out, and tried with what turned out to be a bad bootloader image, it was bricked again and a lot of time went in to recovering it. This all turned out to be a bit of distraction as there is no real reason to want to flash the bootloader in the end, but it led to good hardware and software discoveries (see Ivor’s blog).
Ivor had started a Python library to connect to the RM200 from Linux, using traces from the sync tool. Although I dislike Python, it does seem like a fairly quick and easy way to start interacting with a USB device, so I did the same, and shared the functions I worked out – initially in the process of trying to find ways to get a clean bootloader dump, but also figuring out lots of other functions along the way. Ample log messages in the firmware made this job a hundred times easier. Email not being the easiest way to share and version code, I’ve put my own RM200 library on GitHub, and continue to add functions.