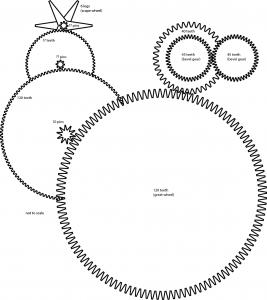
This is the first update for a while on the clock, but we are still working in it. It was a bit cold for spending long in the workshop over winter. Then, as things picked up in spring, there were plenty of other priorities. As well as creating the pattern for the pendulum support casting we now have all the key measurements and positions worked out for the escapement. We have also started work on another missing wheel (but more on that in another post to come).
When the clock was converted to electric drive it was became little more than a gear train from the motor to the drive shaft. It no longer used a pendulum or escapement and unfortunately these were not kept with the clock. The pendulum would have been mounted on a large cast iron wishbone-shaped casting at the back of the clock. The arms of the escapement were also attached to this structure.
The pattern for the casting was made out of a couple of chunks of pine joined together. The basic shape was cut out with a band-saw. A small amount of hand carving was required for fine details and wax fillets were applied to the recessed front edge. Dimensions for the arch were taken from the clock of St. Alkmund’s Church, Duffield. The measurements were taken in situ, from the top of a ladder, while the clock was going. As a result they may not be quite 100% accurate, but very close to the original.
My father approached a couple of local foundries about casting the pattern. I was surprised there were any local foundries left, let alone a choice, but then Derbyshire was the birthplace of the industrial revolution! Neither of us really knew how much it was likely to cost but we were disappointed with the first quote of over £160. In the end we managed to get it for £55, with a 3 week turnaround. We’re still waiting and I’ll post pictures once we get the finished article. It’s going to need a little machining to complete. The base needs to be made flat and a v-shaped groove cut across the top for the pendulum to sit in. It also needs to accommodate two brass plates, one on the front and one on the back, to mount the arms of the escapement.